Users of the popular Steam gaming platform need to pay close attention to chat messages and invites they receive on Steam and elsewhere, as hackers use a new phishing attack to steal accounts.
Steam is the most popular game distribution service on PC. Each year, Valve, the corporation behind Steam, is posting new user records.
Concurrent Steam users, for instance, rose from less than 20 million in the beginning of 2020 to close to 30 million in the beginning of 2022.
While there are other platforms out there, the Epic Games Store, Electronic Arts’ Origin or the Microsoft Store, it is Steam that is the go-to platform for most desktop gamers.
Evergreen games by Valve, such as Counter-Strike, Dota 2 or Team Fortress 2, dominate the charts and help cement Steam’s dominance. Games from third-party developers, for example PUBG, Grand Theft Auto V or Apex Legends, have strong player counts as well.
The popularity of Steam attracts hackers and malicious actors. Some Steam users have invested thousands of Dollars, and more, to buy games, items or digital assets. Stealing these accounts and then selling them entirely or the digital assets they contain, is lucrative.
Browser-in-the-Browser attack targeting Steam users
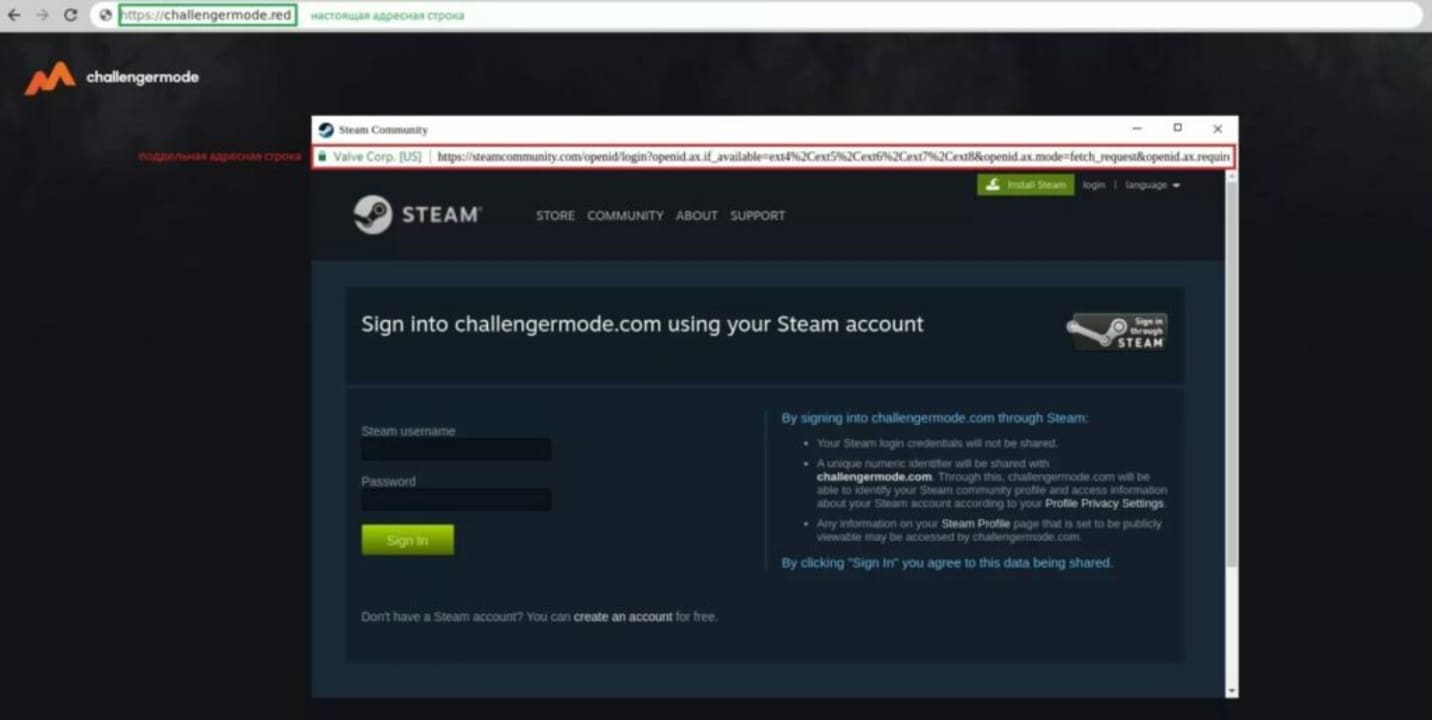
Discovered by security researcher mr.d0x, browser-in-the-browser attacks use fake browsing windows on phishing resources. These fake browser windows are indistinguishable from the real one on first glance. The browser window looks like a popup opened by the legitimate site.
Hackers used the technique since March 2022 to create phishing campaigns that target Microsoft or Google accounts.
Group-IB analyzed the Steam phishing attack, which is ongoing at the time of writing. The attack begins with a message send to the victim on Steam or elsewhere. The attacker uses different messages to get the victim to open the phishing website.
These include the following topics:
- Offers to join a gaming team in a popular game.
- Offers to join a tournament.
- Voting for a favorite eSports team.
- Offers to buy discounted tickets to eSports events.
The attacks are not limited to messages on Steam. Group-IB noticed the use of ads in streaming videos and in descriptions of videos as well to get users to open the phishing website. The text promised free game skins to users.
Notably, most of the messages focus on eSports activities or games that support digital assets such as skins or hats. To put it another way: gamers who prefer to play single-player games are not the main focus of the attack, but they may also be attacked.
How the attack plays out
A click on a link in a message or on a site, or an advertisement, opens the phishing site. It looks like a legitimate website. Most interactive elements on the phishing site, for instance, a button or link, open the fake Steam sign-in popup.
The phishing site checks the system language to display the fake Steam login popup in the same language. Data that users enter is submitted to the server of the attacker right away and verified on Steam.
Users see an error message if the verification data is not correct. The phishing site supports Steam’s two-factor authentication security feature.
Steam users, who use two-factor authentication, see the prompt to type the second authentication code. With it, attackers gain full access to the account of the user. This means, that two-factor authentication won’t help protect against the attack.
The attackers may change the user password, email address, and other account data, before they sell the account or its digital assets.
How to protect yourself against browser-in-the-browser attacks
The phishing attack uses different vectors of attack. Some Steam users may receive messages on Steam, while others may be exposed to it when they view gaming videos. In fact, nothing is keeping the attackers from displaying links on regular websites or as advertisements on search engines.
One of the best protective options is to avoid clicking on links posted by users that one does not know. It may be tempting to get that free skin or to join a tournament, but the danger is real and it is usually better to be safe than sorry.
The phishing site may provide clues or warning signals, but it is well crafted. The domain name of the site may warn users not to enter their login credentials on it, even if the fake Steam login page looks real.
The best option that users have is to avoid entering Steam credentials on third-party sites, even if the login prompt looks real or the offer is tempting.
Steam’s two-factor authentication security feature is of no help, as the phishing site supports it.
A deeper analysis of the phishing website is needed to determine with accuracy that it is not legitimate.